Featured
-
-
Article
| Open Access Reactivity of complex communities can be more important than stability
Reactivity of complex communities can be more important than stability
Ecosystems must be able to bounce back from perturbations to persist without species extinctions. This study uses theoretical modelling to show the importance of reactivity—how species respond in the short term to perturbations—for assessing the health of complex ecosystems, revealing that it can be a better predictor of extinction risk than stability.
- Yuguang Yang
- , Katharine Z. Coyte
- & Aming Li
-
Article
| Open Access Training large-scale optoelectronic neural networks with dual-neuron optical-artificial learning
Training large-scale optoelectronic neural networks with dual-neuron optical-artificial learning
Optoelectronic neural networks are a promising avenue in AI computing for parallelization, power efficiency, and speed. Here, the authors present a dual-neuron optical-artificial learning approach for training large-scale diffractive neural networks, achieving VGG-level performance on ImageNet in simulation with a network that is 10 times larger than existing ones.
- Xiaoyun Yuan
- , Yong Wang
- & Lu Fang
-
Article
| Open Access Parallel window decoding enables scalable fault tolerant quantum computation
Parallel window decoding enables scalable fault tolerant quantum computation
In order to be useful for future large-scale quantum computing, quantum error correction needs to allow for fast enough classical decoding time, while at the moment the slowdown is exponential in the size of the code. Here, the authors remove this roadblock, showing how to parallelize decoding and make the slowdown polynomial.
- Luka Skoric
- , Dan E. Browne
- & Earl T. Campbell
-
Article
| Open Access Extracting medicinal chemistry intuition via preference machine learning
Extracting medicinal chemistry intuition via preference machine learning
Over their careers, medicinal chemists develop a gut feeling for what is a promising molecule. Here, the authors use machine learning models to learn this intuition and show that it can be successfully applied in several drug discovery scenarios.
- Oh-Hyeon Choung
- , Riccardo Vianello
- & José Jiménez-Luna
-
Article
| Open Access Exploring decarbonization pathways for USA passenger and freight mobility
Exploring decarbonization pathways for USA passenger and freight mobility
Rapid adoption of zero-emission vehicles with a concurrent transition to clean electricity is essential to achieve U.S. transportation decarbonization goals. Managing travel demand can ease this transition by reducing the need for clean electricity supply. @cghoehne, @nrel, #NRELMobility
- Christopher Hoehne
- , Matteo Muratori
- & Ookie Ma
-
Article
| Open Access Hierarchical AI enables global interpretation of culture plates in the era of digital microbiology
Hierarchical AI enables global interpretation of culture plates in the era of digital microbiology
DeepColony is a multi-level AI solution for the interpretation of bacterial culturing images in clinical microbiology laboratory automations. Here, the authors show it allows presumptive identification and quantitation of relevant pathogens at both colony- and plate-level.
- Alberto Signoroni
- , Alessandro Ferrari
- & Karissa Culbreath
-
Article
| Open Access A human-machine collaborative approach measures economic development using satellite imagery
A human-machine collaborative approach measures economic development using satellite imagery
A human-AI collaborative computer vision algorithm produces grid-level economic statistics using satellite images and lightweight human annotation, revealing granular development patterns in North Korea and five other least developed Asian countries.
- Donghyun Ahn
- , Jeasurk Yang
- & Sungwon Park
-
Article
| Open Access Knowledge-driven design of solid-electrolyte interphases on lithium metal via multiscale modelling
Knowledge-driven design of solid-electrolyte interphases on lithium metal via multiscale modelling
The application of Li metal electrodes in rechargeable batteries is limited by inherent high reactivity. Here, the authors provide model-based insights into the composition and formation mechanisms of the solid-electrolyte interphase on the µs-scale and suggest design strategies for the interphase.
- Janika Wagner-Henke
- , Dacheng Kuai
- & Ulrike Krewer
-
Article
| Open Access Mutant fixation in the presence of a natural enemy
Mutant fixation in the presence of a natural enemy
Studies on mutant invasion typically assume populations in isolation, rather than part of an ecological community. Here, the authors use computational models to investigate how enemy-victim interactions influence properties of mutant invasion, showing that selection is substantially weakened.
- Dominik Wodarz
- & Natalia L. Komarova
-
Article
| Open Access Automatic correction of performance drift under acquisition shift in medical image classification
Automatic correction of performance drift under acquisition shift in medical image classification
Automatic correction of performance drift caused by changes in image acquisition is key for safe AI deployment. Here, the authors present a solution that restores the expected clinical performance of image classification systems in breast screening and histopathology.
- Mélanie Roschewitz
- , Galvin Khara
- & Ben Glocker
-
Article
| Open Access Remote inspection of adversary-controlled environments
Remote inspection of adversary-controlled environments
Physical unclonable functions (PUFs) normally ensure authentication of small physical objects. Here, instead, the authors observe that also rooms and buildings can serve as PUFs. They apply this insight to monitor the integrity of enclosed environments, such as art galleries, bank vaults, or data centers.
- Johannes Tobisch
- , Sébastien Philippe
- & Ulrich Rührmair
-
Article
| Open Access Predicting discrete-time bifurcations with deep learning
Predicting discrete-time bifurcations with deep learning
Critical transitions and qualitative changes of dynamics in cardiac, ecological, and economical systems, can be characterized by discrete-time bifurcations. The authors propose a deep learning framework that provides early warning signals for critical transitions in discrete-time experimental data.
- Thomas M. Bury
- , Daniel Dylewsky
- & Gil Bub
-
Article
| Open Access Hyper-cores promote localization and efficient seeding in higher-order processes
Hyper-cores promote localization and efficient seeding in higher-order processes
Networks with higher-order interactions provide better description of social and biological systems, however tools to analyze their function still need to be developed. The authors introduce here a decomposition of network in hyper-cores, that gives better understanding of spreading processes and can be applied to fingerprint real-world datasets.
- Marco Mancastroppa
- , Iacopo Iacopini
- & Alain Barrat
-
Review Article
| Open AccessThe promise of data science for health research in Africa
In this Review article, the authors discuss emerging efforts to build ethical governance frameworks for data science health research in Africa and the opportunities to advance these through investments by African governments and institutions, international funding organizations and collaborations for research and capacity development.
- Clement A. Adebamowo
- , Shawneequa Callier
- & Sally N. Adebamowo
-
Article
| Open Access Efficient optimization with higher-order Ising machines
Efficient optimization with higher-order Ising machines
Combinatorial optimization problems can be solved on parallel hardware called Ising machines. Most studies have focused on the use of second-order Ising machines. Compared to second-order Ising machines, the authors show that higher-order Ising machines realized with coupled-oscillator networks can be more resource-efficient and provide superior solutions for constraint satisfaction problems.
- Connor Bybee
- , Denis Kleyko
- & Friedrich T. Sommer
-
Article
| Open Access The reaction-diffusion basis of animated patterns in eukaryotic flagella
The reaction-diffusion basis of animated patterns in eukaryotic flagella
In 1952, Turing unlocked the reaction-diffusion basis of natural patterns, such as zebra stripes. The authors propose a reaction-diffusion model that recreates characteristics of the flagellar waveform for bull sperm and Chlamydomonas flagella.
- James F. Cass
- & Hermes Bloomfield-Gadêlha
-
Article
| Open Access A digital twin for DNA data storage based on comprehensive quantification of errors and biases
A digital twin for DNA data storage based on comprehensive quantification of errors and biases
Archiving data in synthetic DNA offers unprecedented storage density and longevity. To understand how experimental choices affect the integrity of digital data stored in DNA, the authors study the evolution of errors and bias and with a digital twin they supply tools for experimental planning and design of error-correcing codes.
- Andreas L. Gimpel
- , Wendelin J. Stark
- & Robert N. Grass
-
Article
| Open Access The complexity of NISQ
The complexity of NISQ
Our current understanding of the computational abilities of near-intermediate scale quantum (NISQ) computing devices is limited, in part due to the absence of a precise definition for this regime. Here, the authors formally define the NISQ realm and provide rigorous evidence that its capabilities are situated between the complexity classes BPP and BQP.
- Sitan Chen
- , Jordan Cotler
- & Jerry Li
-
Article
| Open Access Multimaterial fiber as a physical simulator of a capillary instability
Multimaterial fiber as a physical simulator of a capillary instability
Capillary breakup in multimaterial fibers is explored for the self-assembly of optoelectronic systems. However, its insights primarily stem from numerical simulations, qualitative at best. The authors formulate an analytical model of such breakup, obtaining a window in the governing parameters where the generally chaotic breakup becomes predictable and thus engineerable.
- Camila Faccini de Lima
- , Fan Wang
- & Alexander Gumennik
-
Article
| Open Access On the visual analytic intelligence of neural networks
On the visual analytic intelligence of neural networks
Visual oddity tasks delve into the visual analytic intelligence of humans, which remained challenging for artificial neural networks. The authors propose here a model with biologically inspired neural dynamics and synthetic saccadic eye movements with improved efficiency and accuracy in solving the visual oddity tasks.
- Stanisław Woźniak
- , Hlynur Jónsson
- & Evangelos Eleftheriou
-
Article
| Open Access Realistic fault detection of li-ion battery via dynamical deep learning
Realistic fault detection of li-ion battery via dynamical deep learning
Accurate evaluation of Li-ion battery safety conditions can reduce unexpected cell failures. Here, authors present a large-scale electric vehicle charging dataset for benchmarking existing algorithms, and develop a deep learning algorithm for detecting Li-ion battery faults.
- Jingzhao Zhang
- , Yanan Wang
- & Minggao Ouyang
-
Article
| Open Access Creating speech zones with self-distributing acoustic swarms
Creating speech zones with self-distributing acoustic swarms
Want to mute or focus on speech from a specific region in a crowded room? Here, the authors built an acoustic swarm that, along with neural networks, separates and localizes concurrent speakers in the 2D space with high precision.
- Malek Itani
- , Tuochao Chen
- & Shyamnath Gollakota
-
Article
| Open Access epiAneufinder identifies copy number alterations from single-cell ATAC-seq data
epiAneufinder identifies copy number alterations from single-cell ATAC-seq data
'Here the authors present epiAneufinder, an algorithm for the identification of single-cell copy number alterations from scATAC-seq data, and explore the clonal heterogeneity in cell populations.
- Akshaya Ramakrishnan
- , Aikaterini Symeonidi
- & Maria Colomé-Tatché
-
Article
| Open Access Capturing dynamical correlations using implicit neural representations
Capturing dynamical correlations using implicit neural representations
Analysis of experimental data in condensed matter is often challenging due to system complexity and slow character of physical simulations. The authors propose a framework that combines machine learning with theoretical calculations to enable real-time analysis for electron, neutron, and x-ray spectroscopies.
- Sathya R. Chitturi
- , Zhurun Ji
- & Joshua J. Turner
-
Article
| Open Access A robust normalized local filter to estimate compositional heterogeneity directly from cryo-EM maps
A robust normalized local filter to estimate compositional heterogeneity directly from cryo-EM maps
Heterogeneity in structural biology data includes potentially valuable information about binding and dynamics. Here, the authors devise, validate and demonstrate a method to quantify local heterogeneity in 3D reconstructions.
- Björn O. Forsberg
- , Pranav N. M. Shah
- & Alister Burt
-
Article
| Open Access A GPU-based computational framework that bridges neuron simulation and artificial intelligence
A GPU-based computational framework that bridges neuron simulation and artificial intelligence
High computational cost severely limit the applications of biophysically detailed multi-compartment models. Here, the authors present DeepDendrite, a GPU-optimized tool that drastically accelerates detailed neuron simulations for neuroscience and AI, enabling exploration of intricate neuronal processes and dendritic learning mechanisms in these fields.
- Yichen Zhang
- , Gan He
- & Tiejun Huang
-
Matters Arising
| Open Access Reply to: Deep reinforced learning heuristic tested on spin-glass ground states: The larger picture
Reply to: Deep reinforced learning heuristic tested on spin-glass ground states: The larger picture
- Changjun Fan
- , Mutian Shen
- & Yang-Yu Liu
-
Matters Arising
| Open Access Deep reinforced learning heuristic tested on spin-glass ground states: The larger picture
Deep reinforced learning heuristic tested on spin-glass ground states: The larger picture
- Stefan Boettcher
-
Article
| Open Access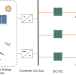 Digital twin based monitoring and control for DC-DC converters
Digital twin based monitoring and control for DC-DC converters
In this work, authors explore DC-DC converter monitoring and control and demonstrate a generalizable digital twin based buck converter system that enables dynamic synchronization even under reference value changes, physical system model variation, and physical controller failure.
- Zhongcheng Lei
- , Hong Zhou
- & Guo-Ping Liu
-
Article
| Open Access Transfer Learning with Kernel Methods
Transfer Learning with Kernel Methods
Transfer learning can be applied in computer vision and natural language processing to utilize knowledge from a source task to improve performance on a target task. The authors propose a framework for transfer learning with kernel methods for improved image classification and virtual drug screening.
- Adityanarayanan Radhakrishnan
- , Max Ruiz Luyten
- & Caroline Uhler
-
Article
| Open Access ADuLT: An efficient and robust time-to-event GWAS
ADuLT: An efficient and robust time-to-event GWAS
Robust genome-wide association study (GWAS) methods that can utilise time-to-event information such as age-of-onset will help increase power in analyses for common health outcomes. Here, the authors propose a computationally efficient time-to-event model for GWAS.
- Emil M. Pedersen
- , Esben Agerbo
- & Bjarni J. Vilhjálmsson
-
Article
| Open Access Machine learning the dimension of a Fano variety
Machine learning the dimension of a Fano variety
Fano varieties are mathematical shapes that are basic units in geometry, they are challenging to classify in high dimensions. The authors introduce a machine learning approach that picks out geometric structure from complex mathematical data where rigorous analytical methods are lacking.
- Tom Coates
- , Alexander M. Kasprzyk
- & Sara Veneziale
-
Article
| Open Access Heterogeneity in M. tuberculosis β-lactamase inhibition by Sulbactam
Heterogeneity in M. tuberculosis β-lactamase inhibition by Sulbactam
Here, the reaction of the suicide inhibitor sulbactam with the M. tuberculosis β-lactamase (BlaC) is investigated with time-resolved crystallography. Singular Value Decomposition is implemented to extract kinetic information despite changes in unit cell parameters during the time-course of the reaction.
- Tek Narsingh Malla
- , Kara Zielinski
- & Marius Schmidt
-
Article
| Open Access Demonstration of an AI-driven workflow for autonomous high-resolution scanning microscopy
Demonstration of an AI-driven workflow for autonomous high-resolution scanning microscopy
Modern microscopes can image a sample with sub-Angstrom and sub-picosecond resolutions, but this often requires analysis of tremendously large datasets. Here, the authors demonstrate that an autonomous experiment can yield over a 70% reduction in dataset size while still producing high-fidelity images of the sample.
- Saugat Kandel
- , Tao Zhou
- & Mathew J. Cherukara
-
Article
| Open Access A deep learning-based stripe self-correction method for stitched microscopic images
A deep learning-based stripe self-correction method for stitched microscopic images
Image stitching in fluorescence microscopy can be a hindrance to image quality and to downstream quantitative analyses. Here, the authors propose a deep learning-based stripe self-correction method that corrects diverse stripes and artifacts for stitched microscopic images.
- Shu Wang
- , Xiaoxiang Liu
- & Jianxin Chen
-
Article
| Open Access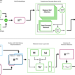 Synthesize high-dimensional longitudinal electronic health records via hierarchical autoregressive language model
Synthesize high-dimensional longitudinal electronic health records via hierarchical autoregressive language model
The paper presents HALO, a Hierarchical Autoregressive Language Model, for generating high-fidelity, longitudinal electronic health records (EHR) data. HALO maintains statistical property, supports machine learning modeling without privacy concerns.
- Brandon Theodorou
- , Cao Xiao
- & Jimeng Sun
-
Article
| Open Access Hardware-aware training for large-scale and diverse deep learning inference workloads using in-memory computing-based accelerators
Hardware-aware training for large-scale and diverse deep learning inference workloads using in-memory computing-based accelerators
Analog in-memory computing promises efficient DNN inference acceleration but suffers from nonidealities. Here, hardware-aware training methods are improved so that various larger DNNs of diverse topologies nevertheless achieve iso-accuracy.
- Malte J. Rasch
- , Charles Mackin
- & Vijay Narayanan
-
Article
| Open Access Critical dynamics arise during structured information presentation within embodied in vitro neuronal networks
Critical dynamics arise during structured information presentation within embodied in vitro neuronal networks
The conditions under which networks of neurons exhibit critical dynamics remains unclear. Here, the authors investigate how simple neural cultures reorganize activity when embodied in a gameplay environment and find that network wide neural criticality arises in nuanced ways.
- Forough Habibollahi
- , Brett J. Kagan
- & Chris French
-
Article
| Open Access Security of quantum key distribution from generalised entropy accumulation
Security of quantum key distribution from generalised entropy accumulation
Security proofs against general attacks are the ultimate goal of QKD. Here, the authors show how the Generalised Entropy Accumulation Theorem can be used, for some classes of QKD scenarios, to translate security proofs against collective attacks in the asymptotic regime into proofs against general attacks in the finite-size regime.
- Tony Metger
- & Renato Renner
-
Article
| Open Access Universal patterns in egocentric communication networks
Universal patterns in egocentric communication networks
Personal communication networks through mobile phones and online platforms can be characterized by patterns of tie strengths. The authors propose a model to explain driving mechanisms of emerging tie strength heterogeneity in social networks, observing similarity of patterns across various datasets.
- Gerardo Iñiguez
- , Sara Heydari
- & Jari Saramäki
-
Article
| Open Access Projecting RNA measurements onto single cell atlases to extract cell type-specific expression profiles using scProjection
Projecting RNA measurements onto single cell atlases to extract cell type-specific expression profiles using scProjection
Many expression deconvolution approaches have been developed to estimate % RNA contributions of diverse cell types to mixed RNA measurements. Here, the authors have developed a complementary approach called scProjection to recover cell type-specific expression profiles from mixed RNA measurements.
- Nelson Johansen
- , Hongru Hu
- & Gerald Quon
-
Article
| Open Access Propensity of selecting mutant parasites for the antimalarial drug cabamiquine
Propensity of selecting mutant parasites for the antimalarial drug cabamiquine
Authors utilize a number of models (mathematical, in vitro and in vivo infection) to analyse pre-clinical and Phase I clinical trial data, in regard to potential risk of resistance associated with a Plasmodium falciparum inhibitor, cabamiquine.
- Eva Stadler
- , Mohamed Maiga
- & Thomas Spangenberg
-
Article
| Open Access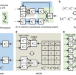 In-memory mechanical computing
In-memory mechanical computing
Here, Mei and Chen propose an in-memory mechanical computing architecture with simplified and reduced data exchange, where computing occurs within mechanical memory units, to facilitate the design of intelligent mechanical systems.
- Tie Mei
- & Chang Qing Chen
-
Article
| Open Access Zero-shot visual reasoning through probabilistic analogical mapping
Zero-shot visual reasoning through probabilistic analogical mapping
Inspired by human analogical reasoning in cognitive science, the authors propose an approach combining deep learning systems with an analogical reasoning mechanism, to detect abstract similarity in real-world images without intensive training in reasoning tasks.
- Taylor Webb
- , Shuhao Fu
- & Hongjing Lu
-
Article
| Open Access Sequence anticipation and spike-timing-dependent plasticity emerge from a predictive learning rule
Sequence anticipation and spike-timing-dependent plasticity emerge from a predictive learning rule
Prediction of future inputs is a key computational task for the brain. Here, the authors proposed a predictive learning rule in neurons that leads to anticipation and recall of inputs, and that reproduces experimentally observed STDP phenomena.
- Matteo Saponati
- & Martin Vinck
-
Article
| Open Access A deep learning method for replicate-based analysis of chromosome conformation contacts using Siamese neural networks
A deep learning method for replicate-based analysis of chromosome conformation contacts using Siamese neural networks
Siamese neural networks are a powerful deep learning approach for image analysis. Here, the authors adapt this method to the replicate-based analysis of Hi-C data and find that it successfully discriminates technical noise from biological variation.
- Ediem Al-jibury
- , James W. D. King
- & Daniel Rueckert
-
Article
| Open Access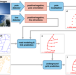 Geospatial mapping of distribution grid with machine learning and publicly-accessible multi-modal data
Geospatial mapping of distribution grid with machine learning and publicly-accessible multi-modal data
Granular geospatial information of distribution grids is needed for various power system applications. Here the authors develop a machine-learning-based model which can accurately map distribution grids in both the U.S. and Sub-Saharan Africa.
- Zhecheng Wang
- , Arun Majumdar
- & Ram Rajagopal
-
Comment
| Open Access The brain’s unique take on algorithms
The brain’s unique take on algorithms
The current gap between computing algorithms and neuromorphic hardware to emulate brains is an outstanding bottleneck in developing neural computing technologies. Aimone and Parekh discuss the possibility of bridging this gap using theoretical computing frameworks from a neuroscience perspective.
- James B. Aimone
- & Ojas Parekh
-
Perspective
| Open Access Toward a formal theory for computing machines made out of whatever physics offers
Toward a formal theory for computing machines made out of whatever physics offers
Learning from human brains to build powerful computers is attractive, yet extremely challenging due to the lack of a guiding computing theory. Jaeger et al. give a perspective on a bottom-up approach to engineer unconventional computing systems, which is fundamentally different to the classical theory based on Turing machines.
- Herbert Jaeger
- , Beatriz Noheda
- & Wilfred G. van der Wiel

 Exploiting redundancy in large materials datasets for efficient machine learning with less data
Exploiting redundancy in large materials datasets for efficient machine learning with less data